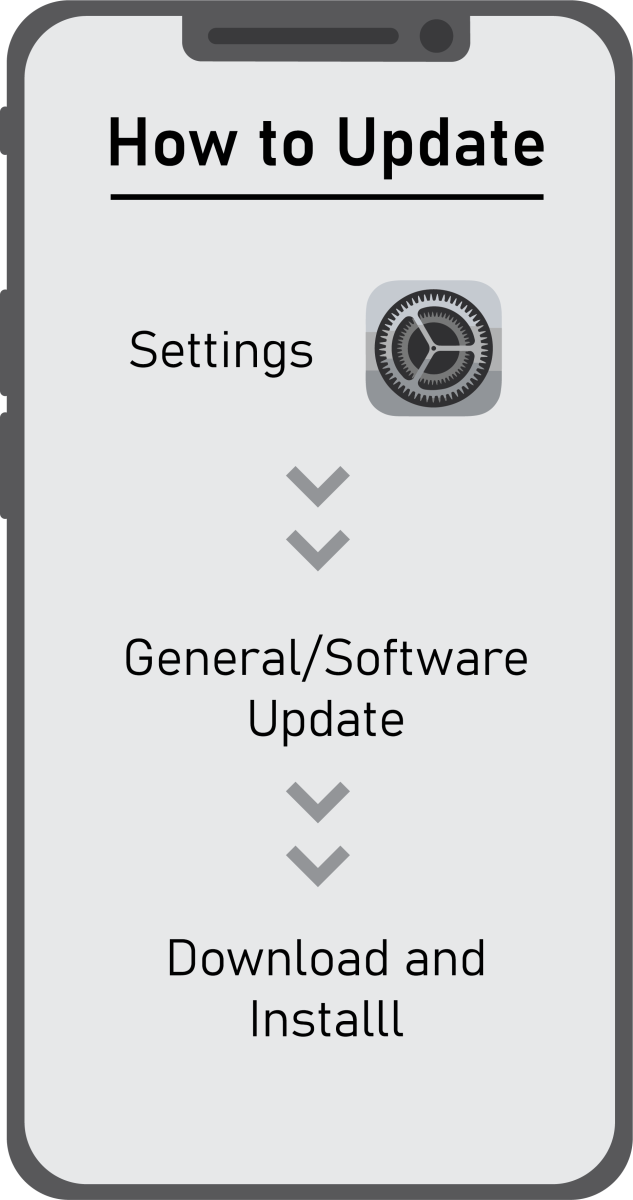
Apple is urging its users to update their devices following the discovery by The Citizen Lab of a vulnerability within Apple’s image rendering libraries. The Citizen Lab, a private research organization known for its work in cybersecurity, discovered the exploit while analyzing a Saudi activist’s phone. Being referred to as ForcedEntry, this exploit takes advantage of the vulnerability and has the potential to allow Pegasus spyware to infect Apple devices.
Pegasus, the 2016 brainchild of Israeli spyware company NSO Group Technologies, utilizes a unique technique referred to as a zero-click attack. Unlike traditional cyberattacks, zero-click attacks do not require any interaction from the user by exploiting zero-day vulnerabilities. Pegasus can exist undetected within a user’s iPhone, MacBook or even Apple Watch while silently collecting and transmitting data associated with messages, calls, location and more. The spyware can also remotely activate a user’s microphone and camera without alerting the user. This data can then be relayed to NSO or any of the governments and private organizations that they have worked with.
NSO has previously been contracted to spy on activists, journalists and even students by nations and organizations around the world. Bahrain, India, Saudi Arabia, United Arab Emirates and Mexican drug cartels have all been implicated in the purchase and usage of Pegasus spyware. Though NSO officially claims to only investigate terrorism, a forensic study by Amnesty International this July revealed “widespread, persistent and ongoing unlawful surveillance and human rights abuses perpetrated using NSO Group’s Pegasus spyware.”
Amnesty International recently released their Mobile Verification Toolkit to allow individuals the ability to identify whether their phone has been compromised by Pegasus. Amnesty’s toolkit is available for both Android and iOS devices. The toolkit does not currently detect any of the other vulnerabilities within Apple’s operating system and cannot be used for laptops.
Global cybersecurity expert Kaspersky Labs notes that Apple devices do not often get viruses because Apple’s operating system keeps each application within a separate virtual space. However, the increasing list of Apple’s common vulnerabilities and exposures, or CVEs, highlights a rising threat to the previously secure space that Apple sat in. Apple’s branding and long-standing history have helped to make it the brand of choice for many students.
Microsoft customers were also greeted with a security update last week. This update will prompt users to abandon their passwords in exchange for what Microsoft hopes is a more secure authenticator through mobile phones. As of a 2020 report by Malwarebytes, Windows remains the more vulnerable operating system. The same study found that, for the first time, Macs are seeing more threats detected per endpoint by a rate almost double that of Windows devices. Regardless of device, students and instructors alike should routinely update devices to protect against vulnerabilities.